Online safety has become more critical than ever, especially in a world where much of our personal and professional lives exist in digital spaces. Recognizing this, Microsoft has been ramping up efforts to enhance user protection.
But it’s not just about building better security tools. According to a recent post on the company’s official blog, Microsoft has also been working closely with international cybersecurity partners to take down one of the most widely used threats targeting individuals and businesses: Lumma Stealer.
This malicious software has been a major tool for cybercriminals, designed to steal sensitive personal data, login credentials, and corporate information. Its takedown marks a significant victory in the fight against cybercrime and highlights the power of collaborative efforts between tech companies and global security networks.
What is Lumma Stealer?

Before getting into Microsoft’s recent efforts to take down Lumma Stealer, it’s important to understand exactly what this threat is—and why it’s such a concern.
Lumma Stealer is a form of malware-as-a-service (MaaS) that’s been circulating in underground forums since around 2022. This malicious tool is designed to steal sensitive personal and business data, which is then sold to the highest bidder on the dark web.
What makes Lumma particularly dangerous is how accessible and stealthy it is. Cybercriminals don’t need deep technical skills to use it, and it’s incredibly hard for traditional security systems to detect. That means it can silently infect systems without users even realizing it.
The primary motivation behind the use of Lumma is financial. Stolen data can be monetized quickly, either by selling credentials, banking info, and other personal records, or by using it for further attacks like identity theft or corporate espionage.
Because of its ease of deployment and difficulty to detect, Lumma Stealer has become a favored tool among cybercriminals—and a serious challenge for cybersecurity professionals worldwide.
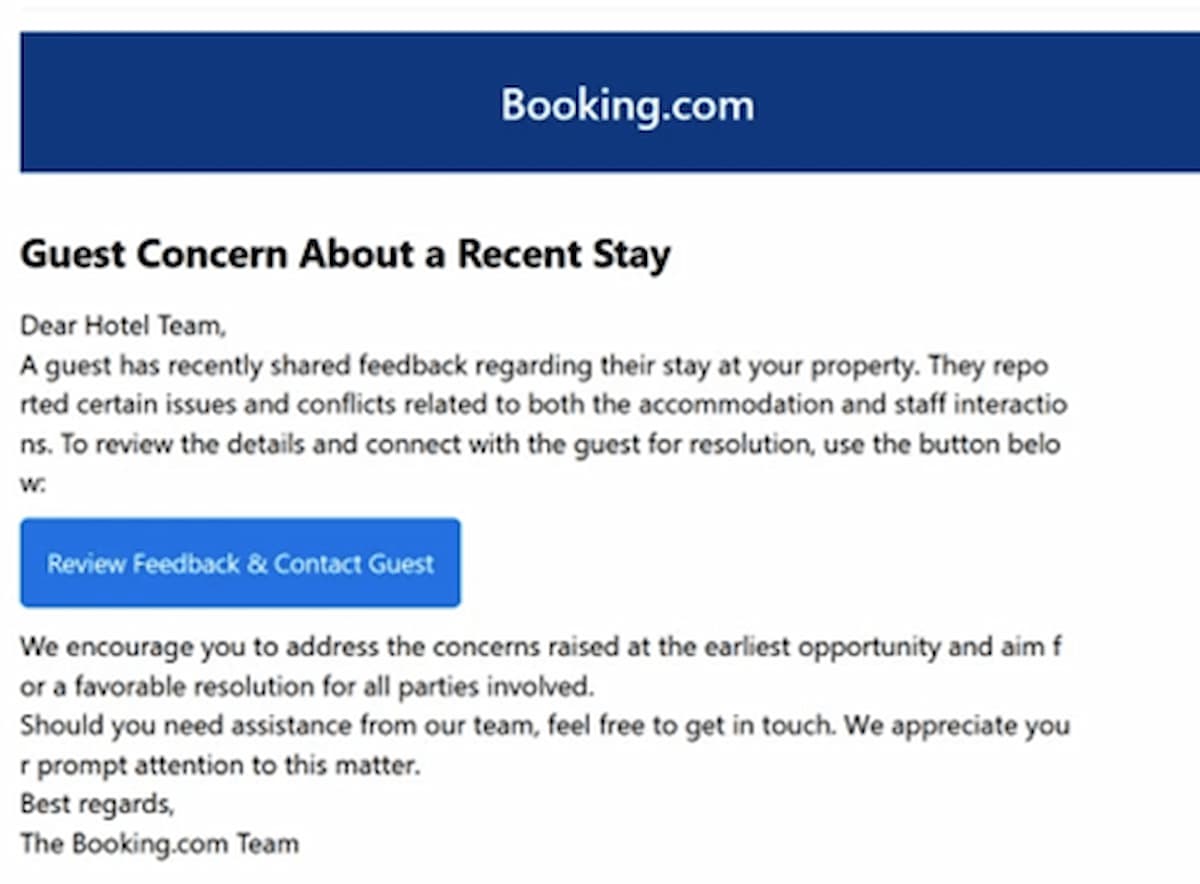
How Lumma Stealer Spreads — and Who’s Behind It
Lumma Stealer isn’t just powerful—it’s also dangerously easy to spread. Cybercriminals commonly distribute it through phishing emails, malicious ads, and fake websites, making it a widespread threat for everyday users and businesses alike.
Back in March 2025, Microsoft’s Threat Intelligence team uncovered a phishing campaign that impersonated Booking.com, the well-known travel service. This attack aimed to trick users into clicking on fake links, unknowingly downloading Lumma Stealer onto their devices.
Investigators have also traced the origins of Lumma back to a Russian developer who goes by the alias “Shamel.” He’s been promoting and selling the malware on Telegram and other local messaging platforms, offering it as a tiered service. The more a buyer pays, the more advanced features and customization tools they receive—essentially turning data theft into a subscription-based business.
This disturbing “business model” has helped Lumma gain popularity in cybercrime circles and has made it even more urgent for tech companies like Microsoft to intervene.
Microsoft leads efforts to try to dismantle Lumma Stealer and protect cybernautas

Lumma Stealer has emerged as one of the most disruptive cyber threats in recent years, and Microsoft isn’t standing idly by. Recognizing the scale of the problem, the company—through its Digital Crimes Unit (DCU)—has joined forces with global cybersecurity agencies to take coordinated action.
On May 13, 2025, Microsoft announced a major legal move targeting Lumma Stealer’s infrastructure. In a decisive ruling, the U.S. District Court for the Northern District of Georgia granted Microsoft the authority to take down more than 2,300 websites linked to the malware’s promotion and sale.
This action followed broader enforcement efforts led by the U.S. Department of Justice, which helped dismantle key online markets that were used to distribute the tool. International partners, including Europol’s European Cybercrime Centre (EC3) and Japan’s Cybercrime Control Center, also played key roles in disrupting Lumma’s operations.
Microsoft has revealed that nearly 395,000 Windows systems worldwide were infected by Lumma Stealer. Additionally, they’ve taken control of over 1,300 domains that had been used for spreading the malware.
These aren’t just symbolic victories—they represent a serious blow to the cybercriminals behind Lumma. The developer behind it, known by the alias “Shamel”, previously bragged about having more than 400 active customers. That number now faces a sharp decline.
However, the fight is far from over. Microsoft and its partners know that cyber threats will continue to evolve. Malware will resurface in new forms, and bad actors will look for fresh ways to evade detection. But this multi-agency effort sends a clear message: cybercrime won’t go unanswered.
Credit also goes to key allies in the cybersecurity space, including ESET, Cloudflare, CleanDNS, and others who contributed technical expertise and support.
If you want to go deeper into the details of this operation, Microsoft has published a full breakdown of the case and its impact on its official blog.