One of the most popular tools among developers is undoubtedly Microsoft Visual Studio Code (VSCode), known for its ease of use and flexibility. It offers a smooth coding experience and supports a wide range of extensions that help boost productivity.
However, according to a report from Bleeping Computer, a cybersecurity researcher has uncovered a concerning issue: several extensions available through the VSCode marketplace were found to contain hidden malware. These malicious add-ons infect Windows systems and secretly use their resources to mine cryptocurrency, without the user’s knowledge or consent.
Here’s what we know so far about this security threat.
It has been reported that several Microsoft VS Code extensions have malware
As previously noted, Microsoft Visual Studio Code (VSCode) is a popular code editor that allows developers to enhance its capabilities by installing extensions, a feature that has made it a favorite in the programming world.
To streamline access, Microsoft created the VSCode Marketplace, a centralized platform where developers can share and install extensions. While this setup makes it easier to customize the editor, it also opens the door to potential risks.
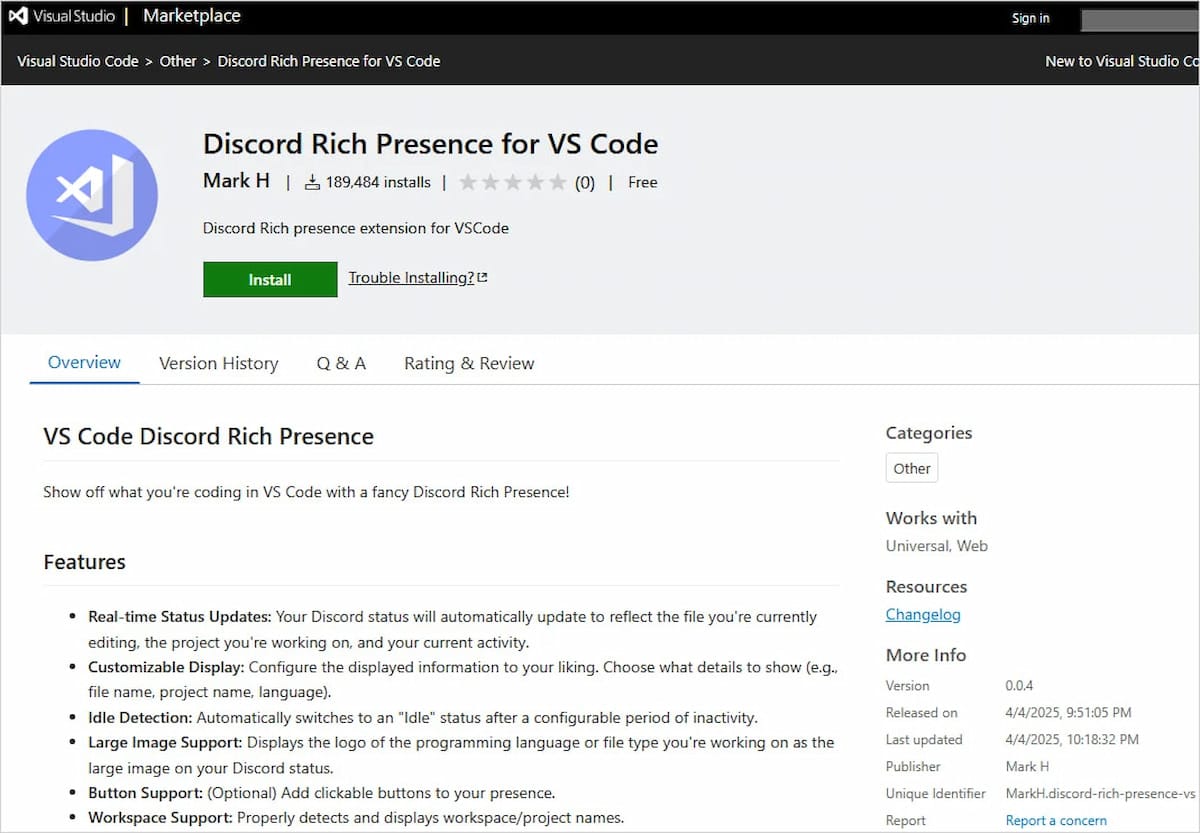
Recently, a security researcher uncovered a serious issue: nine extensions uploaded to the VSCode Marketplace on April 4, 2025, were found to contain malicious code. These extensions, disguised as legitimate development tools, were silently infecting users’ systems with XMRig, a known crypto mining malware. The malware exploits computer resources to mine cryptocurrencies like Monero and Ethereum, without the user’s knowledge or consent.
Here’s a list of the extensions in question:
- Discord Rich Comsense for VSCode – Mark H
- Red – Roblox Studio Sync – Evaera
- Solidity Compiler – VSCode Developer
- Claude AI – Mark H
- Golang Compiler – Mark H
- CHTGPT Agent for VSCode – Mark H
- HTML Obfuscator – Mark H
- Python Obfuscator – Mark H
- Rust Compile for VSCode – Mark H
Combined, these extensions have reportedly been downloaded over 300,000 times, though some of that figure may be inflated to make the extensions appear more popular.
Despite being reported by researcher Yuval Ronen, Microsoft had not yet removed the malicious add-ons from the marketplace at the time of reporting. The fact that they remained available raised concerns about the platform’s vetting process and the potential scale of the infection.
This situation highlights the importance of caution when installing third-party tools, even from official sources, and suggests that more robust oversight is needed to protect developers from hidden threats.
What do VSCODE malicious extensions do in Windows?
It’s crucial to understand that when these malicious extensions are installed, they immediately fetch a PowerShell script from an external source and execute it on the system.
After this hidden operation, the extension quietly installs the real, expected tool it pretends to be, so users remain unaware that anything suspicious has occurred. That script performs several key actions: it disables system protections, grants itself administrator-level permissions, ensures it stays active across reboots, and finally, downloads and launches the cryptomining software.
To remain hidden, the script creates a scheduled task disguised under the name "OneDrivestartup"and injects a command into the Windows Registry so the miner loads whenever the system boots.
It also disables critical services like Windows Update and Windows Media-related processes, and adds its own folder to the antivirus exclusion list, preventing Microsoft Defender from flagging or removing it.
If the malware can’t initially run with admin privileges, it attempts to gain them by impersonating a trusted system file and using DLL hijacking through mlang.dll, a tactic that allows it to bypass standard restrictions.
Once active, the malware silently uses your computer to mine cryptocurrencies—specifically Monero and Ethereum—draining processing power and increasing electricity usage without the user’s knowledge.
If you’ve installed any of the affected extensions, immediate action is required. It’s not enough to simply uninstall the extension—you also need to track down and delete the miner, remove any related scheduled tasks, clean the malware’s working directory, and erase any registry entries it created.